I use and advocate secure authentication, verification, and encryption methods. Naturally, I have used 2-Factor-Authentication for a long time wherever it is available (Google, Facebook, Dropbox, and many others). In addition, my computers and mobile devices use Full Disk Encryption, protecting my data at rest.
The YubiKey is a small USB device that augments different authentication methods to accomplish these tasks. I recently purchased two of YubiCo’s latest model, the YubiKey 4 to help me with 2FA and FDE.

I could not find much entry-level information on how to set up a YubiKey with BitLocker, the FDE solution of the Windows operating system (specifically, Windows 10). YubiCo itself only offers a guide for developers of FDE software (PDF). To help others, the following sets out the steps I used to implement FDE on my Windows 10 computer with a YubiKey 4. This is partly based on a YubiCo forums post but includes more information.
My system uses the following:
- A mainboard with a Trusted Platform Module (TPM) chip
- Windows 10 Pro (build 1703)
- YubiKey 4 and the YubiKey Personalization Tool
Preparations
If you have never used BitLocker, How-To Geek provides detailed and helpful instructions – You will need to configure your YubiKey before you set up BitLocker. If you already use BitLocker, you can still use your YubiKey, but you will need to change your BitLocker PIN or password.
By the way:
I had already enabled BitLocker, but I used this opportunity to upgrade my encrypted drives from the default AES 128 algorithm to the more secure XTS AES 256 – Chris Hoffman wrote thorough instructions at How-To Geek (that article does not account for XTS AES. The procedure is exactly the same, however. Simply chose XTS AES 256 instead of regular AES 256). This step is entirely optional.
[DE: Es gibt auf Gunther’s Blog auch eine Anleitung auf Deutsch.]
You need to know that using the YubiKey for BitLocker requires a static password. BitLocker FDE does not support more sophisticated authentication methods such as challenge-response. However, we can a) configure the YubiKey to create a long, secure password, and b) augment the password stored on the YubiKey with a memorized prefix (or postfix, if you prefer).
Use with or without a Trusted Platform Module
The TPM in my computer is the primary protection for the BitLocker keys. These keys, in turn, are protected by a 6-20 character PIN that needs to be input at startup. This so-called PIN may also include non-number characters, i.e. letters.
If your computer does not have a TPM, additional steps are required to use BitLocker. How-To Geek provides detailed and helpful instructions on BitLocker setup with and without a TPM. Without a TPM, the password (as opposed to the PIN used in conjunction with a TPM) can and should be longer than 20 characters. Do not be fooled into thinking that the non-TPM option is therefore more secure; it is definitely not.
Configuring the YubiKey
Plug your YubiKey into a free USB port and open the YubiKey Personalization Tool. Follow the next steps as described in these screenshots.
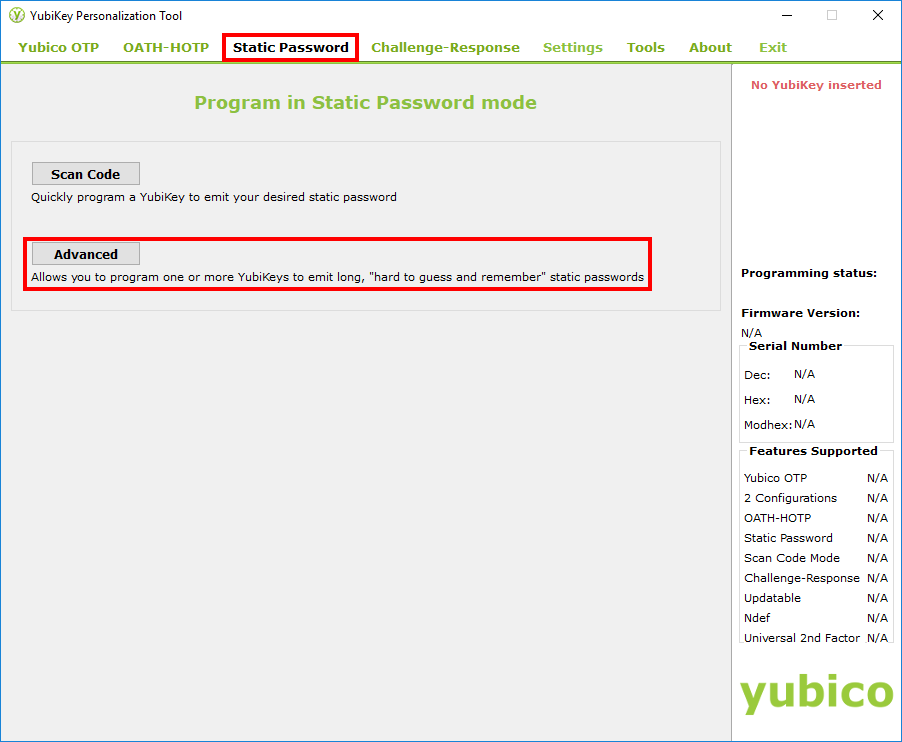
Click on “Static Password”, then “Advanced”.
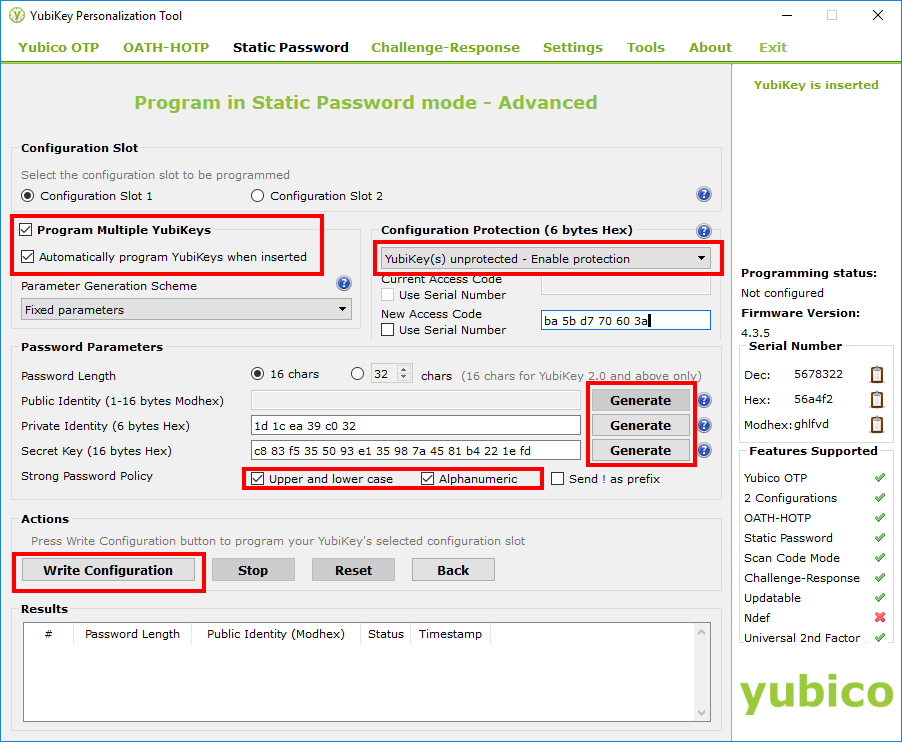
- Pick the slot into which you want to write the PIN/password.
- I used two YubiKeys to have a backup, so I checked “Program Multiple YubiKeys” and had them automatically written to. It is important to use “Fixed parameters” for the Parameter Generation Scheme, otherwise your backup YubiKey would store a different password.
- I chose to protect the configuration for slot 1. This is not a security feature, but helps against accidental deletion of your configuration.
- Depending on whether you use a BitLocker PIN (with a TPM) or a password (without a TPM), chose the proper password length. I use a PIN, which has a 20 character limit as described above. In this example, my memorized prefix would have four characters and the rest of the PIN stored on the YubiKey has 16 characters.
- Check these boxes to include upper- and lowercase letters and the full alphanumeric set of characters.
- Click “Generate” next to each active field. Each time, the Personalization Tool will create a different identity. Note that this is not the password that is later written to the YubiKey – the Personalization tool never shows you that.
-
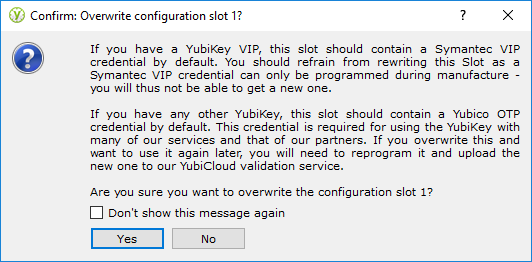
If you write the password to configuration slot 1, the YubiKey Personalization Tool will ask you to confirm this step. Just make sure you had not anything in that slot before.
- When you are satisfied with your settings, click “Write Configuration”. You will receive a confirmation that it worked. If you are programming multiple YubiKeys, you can now disconnect the first and plug in the next YubiKey.
- Each YubiKey you write to will show up on a new line in the “Results” field.
Configuring BitLocker
How-To Geek provides detailed and helpful instructions on BitLocker setup. The following shows the steps where the YubiKey is used.
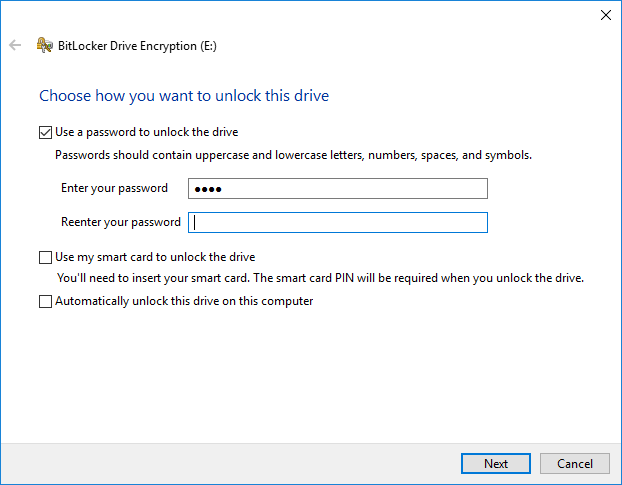
While setting up BitLocker, you will be asked for a PIN or password. First, type your memorized prefix.
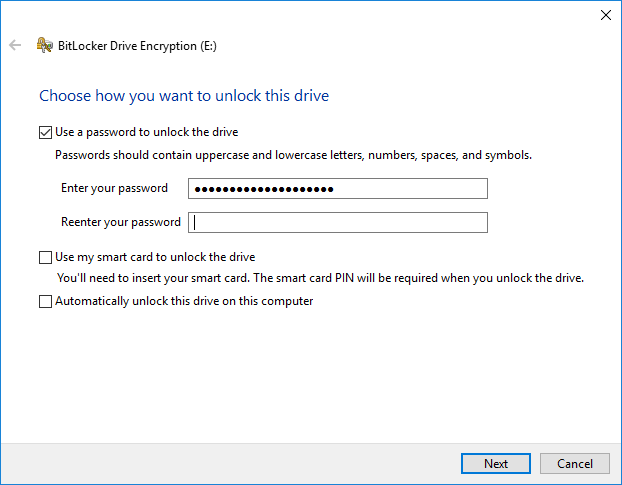
Then, still in the same PIN/password field, insert your YubiKey and tap it. It will then fill in the password it stores.
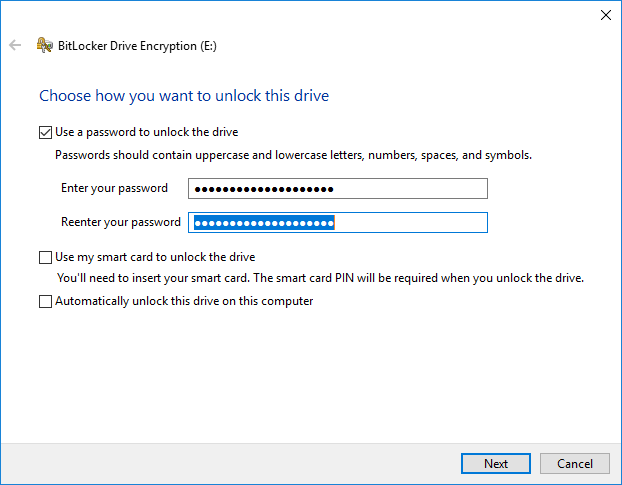
Repeat this step with the password confirmation/reentry field. First, type your prefix, then tap your YubiKey to insert its stored password. (If you prefer a postfix password, reverse the process: Tap the YubiKey first, then write your postfix.)
Click “Next” and BitLocker will continue its process of encrypting your drives. BitLocker will ask you to go restart your computer once to confirm that everything works. This is where you enter your PIN/password as you have done when you set it: Enter your prefix, insert your YubiKey, tap the YubiKey.
After this check and the encryption is done (which can take a long time), you can check the status of BitLocker in the Control Panel, on the command line and with PowerShell (both in Administrator mode) with the command “manage-bde -status”.


Thanks for sharing, great explanation. What happens after you’ve enabled Bitlocker? Does logging into windows unlock the drive, or does that happen during boot? I’m just wondering at what point the Yubikey comes back into play.
Thank you, I’m glad this is helpful.
BitLocker operates and decrypts the drive before the Operating System boots up. So the YubiKey comes into play right after you press the power button. The YubiKey simply holds one part of the passphrase (or “PIN”, as Microsoft calls ist), the other part is your memorized prefix (or postfix). Upon boot, BitLocker shows you a simple screen with a password/PIN prompt; this is when you enter your prefix, insert the YubiKey, and tap it to complete the password/PIN. The OS then completes its boot. Logging into Windows comes later and is not related to encrypting the BitLocker drive.
Does this help?
But the password/PIN is static – What use is that ? (PPS – Pretty Poor Security)
It needs to change on every boot
I would not characterize BitLocker as Pretty Poor Security, but Microsoft can describe it better than I.
As for your proposal that the BitLocker PIN “needs to change on every boot“, what method would you propose? A TOTP/HOTP solution comes to mind, but BitLocker currently does not support this (as stated in my post), and in fact does not support dynamic PINs at all.
However, would this even result in additional security over the method described in my post? I doubt it. For one, the PIN is only a second factor to the TPM, and the TPM protects the PIN as described in my post. The prefix or postfix to the PIN stored on the YubiKey could be described as a third factor (TPM factor + YubiKey hardware factor + prefix/postfix knowledge factor). This would not be different with, for example, TOTP/HOTP – whether the hardware factor is a YubiKey (with a static password) or a smartphone with a TOTP/HOTP app, both are hardware factors; both offer different advantages and disadvantages.
You’re missing the point. They are describing FDE with a static password or pin programmed into a physical device you probably leave in or next to the computer poor security. It’s not too far off from writing your password on a stickie under your keyboard. Sure, it’s cool to be able to use your yubikey to store your password, but you’re still storing it in a way anyone could use it.
They are also stating that greater security would be some form of FDE that has a less easy to determine password each. You’re operating on a false pretense as though the password being stored on the Yubikey somehow renders it safe. It doesn’t. If I can get your yubikey, I can either touch, or hold the contact and type your password into notepad in the clear. You already know this, you’re trying to ignore how vulnerable it is. You’re essentially cheating the „thing you know + think you have“ portion of the equation of security. You’re neutering the „know“ portion by typing the password into something that stores it for you.
It definitely protects your from shoulder surfing which is underestimated attack vector in targetted attacks.
Wait doesn’t the yubikey read your fingerprint when you tap it to send the password?
No, it does not. The YubiKey cannot read a fingerprint, but only records that the button is tapped.
I think you are missing the point. Because there is no such thing as “perfect” when it comes to security, there are no absolutes. Security is best thought of as an onion…it has layers. Now, given the hardware and software limitations the author describes using his method would be better than just using a standalone memorized pin. Here’s why: the memorized pin is kept in memory and scrambled by the TPM when in use so nobody has access to it. So why use a Yubikey at all instead of just a memorized pin? Because cameras (and indeed even clever methods of using microphones) can capture your keystrokes, revealing your password. The addition of the Yubikey password ensures this doesn’t happen (at least until after you’ve configured it). Additionally, because the Yubikey password is long, random and not memorized you cannot be tortured to extract that information as long as you commit to not memorizing it…because all you need to memorize is your prefix. If you know you are about to be captured or seized you can quickly destroy the yubikey and thus render the password inaccessible even to you so your data cannot be accessed even in the event of torture or coercion.
And this also goes without saying, a longer password is harder to guess at, its also harder to remember, thus a prefix+keyPassword kind of helps give you the best of both worlds
Does a static PIN matter much when the data remains static? I am not assuming you think its feasible to re-encrypt the drive on every boot…
Wouldn’t be easier to use the Yubikey 4 as a smart card? Is it possible? Is it possible to follow those same steps using the cheaperSecurity Key by Yubico instead of the Yubikey 4? Thank you for the clarifying post.
The YubiKey 4 works as a Smart Card, yes. The YubiKey Security Key does not. (https://www.yubico.com/solutions/smart-card/)
Indeed it might work to use the YubiKey 4 in this manner, but I do not have a Smart Card reader.
The YubiKey 4 and 5 are both a smart card reader and a smartcard.
Identifies as a Microsoft USB CCID smart card reader and NIST SP 800-73 PIV smart card using the base Microsoft driver.
Too bad that the smart card cannot be used to unlock BitLocker before Windows boots (I tried and found it out the hard way).
So I guess the most secure option would be to use a PIN with pre/postfix plus static password from the YubiKey, and a USB memory stick for unlocking BitLocker.
If I do not enter a password for a protected drive at the boot time, what will happen? Can I load the drive later (if this is not a system drive)?
Yes, you can load a non-system drive later. How and when you need to enter the key depends on your specific setup, so I can’t really speak to that.
In case anyone is trying to setup on a tablet ( like a Surface ) then to avoid a lot of pain/Googling/coffee/screaming … please note that the „pin/password“ option will never be shown when enabling Bitlocker unless you enable:
Computer Configuration\Administrative Templates\Windows Components\Bitlocker Drive Encryption\Operating System Drives\ Enable use of Bitlocker authentication requiring preboot keyboard input on slates
https://blogs.technet.microsoft.com/askpfeplat/2014/07/13/bitlocker-pin-on-surface-pro-3-and-other-tablets/
Once that is set, you should now be able to set a password via the Yubikey ( 5 NFC in my case )
Thank you for your advice!
What if the TPM prevents the input via tap on the YK? That’s what my device does. The previous one without TPM worked as you described but the new one isn’t because the TPM sort of blocks the key input via USB during the boot. Any suggestions? (Could also be done in German, if you prefer)
Unfortunately, I can’t help you with this – I have never experienced this issue (and I use a TPM). Sorry! 🙁
The Yubikey only emulates a keyboard, the TPM doesn’t block input devices. Sometimes enabling “Fast Boot” skips the detection of such devices to speed up the boot process. Try to disable this feature in the UEFI.
Can I use Yubikey5 smart card feature with bitlocker?
Of course I’m talking about using bitlocker after the system is booted – with another partition for example.
To my knowledge, that is unfortunately not possible. However, my knowledge stems from my original setup and therefore might not be current. Maybe it works in the meantime?
When you say tap yubikey when entering password for setup what do you mean?
I mean that you should insert the YubiKey into a USB port and then tap (lightly press) the golden button in the middle.
Do I need to tap the button later every time I boot my system or I can just leave key there without touching it later. (I am planning to hide the key at the beck of my PC and use it only when I leave office for holidays)
With the setup I describe here, the user needs to tap the YubiKey button every time the system boots. This is because here the YubiKey will not/cannot output the stored passphrase unless the key is tapped. Also, I would consider such a setup as unsafe. The idea behind the setup I describe is that the user keeps the YubiKey under her/his control. If the YubiKey remains plugged into the computer at all times, a malicious person would only need to know the prefix/postfix phrase, eliminating the 2-Factor-Authentication.
I’m new to all of this so please excuse the basic nature of my questions. First some background. My new PC has TPM, Windows 10 Pro. I have a Yubikey 5. I want to encrypt one SSD partition (drive). I leave my PC on but in sleep (not hibernation) over night. Windows Task Scheduler wakes it during the night to run a backup to my NAS, and again to run a backup to a cloud service.
My questions: Am I correct in assuming that so long as the PC has not rebooted during the night, it will have access to the encrypted drive without having to reenter credentials? Also, my need for data security is medium at best. Nations won’t fail if my data gets in the wrong hands. That said, does the above approach seem reasonable for a home PC?
Thanks for the great article!
HI the Yubikey personalization tool no longer, exist it has been replaced by the Yubikey manager. I can’t seem to find the options your are mentionning. Any chances of updating your doc to the new software? 🙂
I was able to download the personalization tool and configure a static password on slot 2 of my Yubikey.
Thank you Daniel, I’ll try to do that – can’t guarantee it, however.
One thing to know about the Yubikey that’s important and not sure if mentioned in the OP or not, but you tap it quickly to generate a completely random code from slot 1 which, in most cases already is utilized. I use mine with Duo Security MFA for things like accessing our BitWarden vault and with Duo Security enabled MFA in Microsoft 365 (which also requires some preconfiguration in Azure Active Directory and a Microsoft 365 Business Premium or higher tier license). Slot 2 is for an alternative usage like this static password. You long tap the Yubikey for it to spit out what is stored in slot 2 vs slot 1.
Great article on using the Yubikey in this manner and especially mentioning 256 vs default 128-bit encryption. My 128GB Samsung metalic case flash drive died on me tonight 🙁 Which not only means I had to key in a nuclear launch code from my 365 account to get back into my laptop, but also will have to resetup easy boot and drop all my ISO’s back onto a new flash drive after obtaining a replacement. So I figured now would be a good time to look at using the Yubikey to get into my encrypted bitlocker drive instead of the flash drive method.
Thank you for your valuable feedback!
I configured my Yubikey(s) to log into Windows , using slot 2 (slot 1 already has many services/ sites configured for 2Fa, so can’t use that. Would setting up my keys for Bitlocker overwrite Slot 2 and therefore erase my setup t log into Windows (thereby having to forfeit that and revert back to a basic password or PIN for Windows? If so, I think I’ll stick with my 9 digit Bitlocker password and keep what I have in place. Thoughts?
If you use the method I wrote up, this would overwrite your slot 2. So you would not be able to use it both ways.
Whether it would be “better” (even the definition of “better” could be debated) to use the Yubikey for BitLocker or Windows logon depends on your threat model. If it is for a computer that runs more or less uninterrupted, it may be more useful for Windows logon. If it is for a portable computer that is turned off when you’re on the move, it may be better to use it for BitLocker. Of course, it is also a question of convenience for you.
Laptop mostly stays put on my desk. Only travels during vacations.
One benefit – using a really long BL password (I use a 9 digit PIN now). I’d still need to enter my Windows username/password regardless of method so no change there. So I guess it would “harden” my security more (going from 9 digits to, say, 40 alphanumeric) although how much I don’t know.
In case of a lost key I’m screwed either way and need to use recovery (I think). Would it be harder to regain entry via BL vs Windows?
Yours is the only post I’ve run across describing using using a Yubikey to open BL. Has Yubico put out a “how to” tutorial similar to yours for BL like they do for Windows logon? Is there a YouTube tutorial?
So just to clarify Bill – you’re talking about using the Yubikey to log into Bitlocker, not Windows? I start at bootup by logging into Bitlocker first, then I get the Windows login screen and use my Yubikey for that.
AFAIK, with a notepad opened, tap the yubico key will see the password in plain. it’s really not secure!!!!!
What do you mean? I opened Notepad and then used my key to access a site. Nothing shows up in Notepad.